I love ninite.com for helping windows users get their computers sorted. I recommend it a lot and I wanted a screenshot I could point people to, so this is it.
Category Archives: Technology
HP Compaq 6910p
I just got one of these. My plan is to install Linux on it and use it whenever I’m upstairs. I’ll let you know how things turn out.
Pages 5
Well, this sucks.
This sucks too.
Problems with ObamaCare
Quite apart from the wisdom of interfering with great swaths of the economy to create new entitlements, there is the practical matter of making it work. And that’s proving to be a problem for people working on the Obamacare web site at HealthCare.gov:
The better way to do things is a school of software development called Agile — it’s been around since the 1950s, was basically codified in the early 2000s, now has a whole non-profit devoted to it, and is the dominant form of software design in teams. Rather than moving from one static stage to the next, it emphasizes constant iteration and testing, with prototypes building on prototypes so the endpoint is something that works. The only problem, from a government perspective, is that you need to be comfortable with not knowing exactly that they will look like.
Yes. Just because a type of software development got us to the moon (back when 1K of RAM was a lot) doesn’t mean it’s the right approach to use in the 1990s. Or especially the 2010’s.
That’s one lesson from software development. Here are some others:
1) avoid building centralized systems. The mainframe has given way to minicomputers and PCs then a client-server world and now a web of devices, browsers, and various types of service providers. Web 2.0, baby.
Where does a centralized “Five Year Plan” approach to governing fit in a world of decentralized independent actors?
2) have the right type of abstraction. A spinning metal disk has nothing in common with a USB stick nor with an internet connection, but I can save a file on any one of them with the same program. That’s because there is an abstraction called a file system, and my word processor doesn’t really care what the hardware looks like: it can be silicon, magnetic disks, or something in the cloud. Software drivers for each type of hardware present a common interface that makes them all look the same to the word processor.
A centralized approach to governing doesn’t permit there to be appropriate abstractions. A mix of federal, state, and local governments, with large and small commercial and nonprofit organizations, allows you to have abstraction. Each one does what it needs to do and only that.
Bash Initialization
Every time I monkey with my .profile or .bashrc file I regret it.(.profile is what graybeards like me use instead of using .bash_profile like all the young people who won’t stay off my lawn.)
If you’re like me, you get those confused all the time, so let’s go to the bash(1) man page. (Amazingly, it is a man page and not an info node. Ahem.) Here’s the salient bit of that 37,000 word tome:
When bash is invoked as an interactive login shell, or as a non-interactive shell with the –login option, it first reads and executes commands from the file
/etc/profile, if that file exists. After reading that file, it looks for~/.bash_profile,~/.bash_login, and~/.profile, in that order, and reads and executes commands from the first one that exists and is readable. The –noprofile option may be used when the shell is started to inhibit this behavior.When a login shell exits, bash reads and executes commands from the files
~/.bash_logoutand/etc/bash.bash_logout, if the files exists.When an interactive shell that is not a login shell is started, bash reads and executes commands from
~/.bashrc, if that file exists. This may be inhibited by using the –norc option. The –rcfile file option will force bash to read and execute commands from file instead of~/.bashrc.When bash is started non-interactively, to run a shell script, for example, it looks for the variable
BASH_ENVin the environment, expands its value if it appears there, and uses the expanded value as the name of a file to read and execute. Bash behaves as if the following command were executed:
if [ -n "$BASH_ENV" ]; then . "$BASH_ENV"; fibut the value of the
PATHvariable is not used to search for the file name.
Got all that? The key is that your .profile is read first for login shells and .bashrc for non-login shells. There’s no reason why you should ever worry about what order they get invoked in, because there’s no reason to invoke them both at all. Except if you want to observe the DRY principle. In which case they should both invoke a separate startup file of your own design.
Banish the Blue LED
Someone has discovered another reason to ban the blue LED:
In a study involving hamsters, researchers found that blue light had the worst effects on mood-related measures, followed closely by white light. (Via.)
I’m glad the blue LED was finally invented, and I’m sure my life is better for it in countless ways. But that doesn’t mean it has to be slapped onto every gadget in my house. I’ve got a USB charger that I have to keep in the basement, because it has the brightest single LED (blue of course) I’ve ever seen, and if I use it in the bedroom, or even in the hallway, it affects my sleep.
Miscellaney
It’s been awhile since I blogged, so here are a few things that I might have blogged if I blogged much.
Windows has environment variables, because Microsoft used to steal ideas from Unix. But they never really understood them, so the tools they provide to configure your environment are crappy. Enter REE, the Rapid Environment Editor. (Via.)
Serenity Crew, where are you?. (Via.)
The pinnacle of the typewriter-maker’s craft, introduced 50 years ago. (Via.)
Ten Years
iTunes Confusion
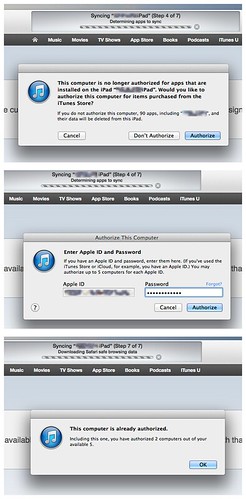
Apple has never impressed me with their ability to have two different devices synchronize with each other. But they’ve got plenty of hubris, so they keep trying. Take the app store. (Please!) Here’s what happens when I sync my iPad: it tells me I need to authorize my computer to sync to it, I authorize it, and then it tells me never mind, because the computer is already authorized.
OK. That explains it, then.
Software Update
In the mid-1990’s I worked for a telecommunications firm that was trying to make a set top box for interactive television. (This was even as the internet was exploding. Read Michael Lewis’ The Next Next Thing to find out what the “B Team” was working on.) One of the things I spent a lot of time on was “software update.” We needed a way to securely update the operating software in the device, and we wanted to do it while connected to our network, because the cost to roll a truck and have a technician do it was prohibitive.
A few years later, I was working for a different company trying to innovate in the electrical power industry. (I know, it was hopeless. But I was young and naive.) Anyway, we had the exact same problem: securely updating the software in a networked device. It’s a problem that’s fraught with difficulties.
As it happens, both of those ventures flamed out, so I never got to be part of solving that problem. But this morning, as I was eating my oatmeal, I saw that someone else seems to be doing it:
Not only solved, but untethered. Yay Apple.